A captive portal is a network that forces an HTTP client to see a special web page (usually for authentication purposes) before using the Internet normally. A captive portal turns a Web browser into an authentication device. These are commonly used on wifi networks where authentication to the private network is done via a login browser page, rather than via the use of a WEP or WPA2 key, for example in some coffee shops and airports, and hotspot providers such as The Cloud and ATT-Wifi.
On Apple devices, if a captive portal is identified, a special application in /System/Library/CoreServices called Captive Network Assistant.app is opened. This is a very limited browser, separate to Safari, with no address bar or navigation buttons.
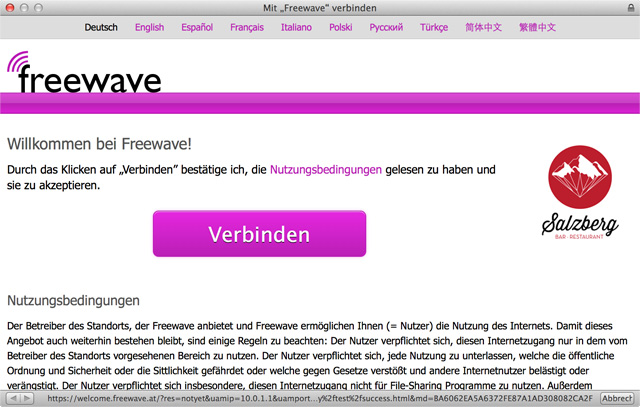
An example window in Captive Network Assistant
Sometimes, the limitations of this browser prevent successful authentication to the wifi network, if the network hasn’t been configured accordingly. In my organisation the end user needs to download a configuration profile in order to connect to our 802.1x protected network (Eduroam). The download of the profile is not possible from within Captive Network Assistant.app due to the limited functionality of the app, and must be done from a full internet browser such as Safari.
In OS X up to 10.9 Mavericks, the presence of a captive portal was established upon connection to an open wifi network by attempting to connect to the following URL, which has the key ProbeURL:
http://www.apple.com/library/test/success.html
This is determined in the following file:
/Library/Preferences/SystemConfiguration/CaptiveNetworkSupport/Settings.plist
You will notice in this file that some of the popular HotSpot Providers have their own settings, and orange.fr is disabled entirely.
I’m not clear whether the necessary response is just a HTTP 200 (“OK”) response, or whether it checks the contents of the page (HTML containing the word “success”).
It is therefore possible to prevent the popup by allowing specific access through the captive network to this specific page only, or spoofing the page. In my organisation, fake root DNS is used to prevent the pop up [note: I don’t know how that works so don’t ask me!].
(On your own Mac, you could take steps to prevent the popup appearing if you wished, by deleting or renaming Captive Network Assistant.app, or changing the Settings.plist to a localhost page, or creating an entry in /etc/hosts file to redirect the ProbeURL to a localhost page. There are umpteen blog/forum posts about doing this, such as this one.)
In Yosemite, something changed. In our organisation, the pop up came back. Why? Simple (once you know): Apple changed the ProbeURL to a new location:
http://captive.apple.com/hotspot-detect.html
Who knows why Apple decided to change this, but I hope if you’re diagnosing wifi popup problems in your organisation, this will help you change your DNS settings accordingly.

The reason, I believe, is that http://www.apple.com now defaults to https, so attempts to access it through a captive portal will fail.
LikeLike
I don’t think that’s true, because both the old and new ProbeURLs are still available via a normal browser (and the new one is not https either).
LikeLike
Actually I’m thinking Jon might be on to something. If Apple wants to turn on HSTS for their domain, it’s going to need to move this service to a non-HTTPS enforcing URL, lest they have to build some weird edge-case.
LikeLike
Ah yes, that could be true. Future-proofing.
LikeLike
Thank you for this blog post. This is exactly the info I was looking for, particularly the profiles limitation part.
LikeLike
Anyone have issues trying to use the full browser workaround over CNA? Whether yes/no, do you typically fire up the browser and try visiting some website that should then trigger the captive portal redirect OR specifically visit the captive portal URL in the browser that’s fired up? Although the captive portal URL isn’t always an easy to remember one being IP Address based sometimes.
I noticed I kind of had issues with the browser workaround unless perhaps CNA disabled as per the sample link in this blog post. At times, it wouldn’t load the captive portal in browser if CNA was running, unless perhaps you knew the specific captive portal URL.
Also, this is an interesting related read: https://discussions.apple.com/thread/5258403
LikeLike
Would anyone consider these limitations a bug or expected behavior? Just wondering if anyone filed a bug report with Apple. I don’t think I see any cross-posted on OpenRadar: http://www.openradar.me/search?query=captive+network
LikeLike
What bug exactly ?
Actually Yosemite probe your Captive wifi with a bunch of URL, it is impossible to know them all. Nox the URL is even randomized + subfoldered with unique ID. Apple certainly does it to ensure that the CNA is never hackly hidden…
By my side, I only show my ToS in the CNA, and I dont know how to hide it, once my Tos accept-button is clicked. Some help please
LikeLike
Pingback: TECNOLOGÍA » drduh/OS-X-Yosemite-Security-and-Privacy-Guide · GitHub
Anyone have any experience on profile download from captive portal support for Windows 10, Windows 10 Mobile? I believe one or both of those should be supporting it, but there’s not much info out there regarding it.
LikeLiked by 1 person
Thanks. This was JUST what we needed in order to make our laptops talk to the Open Directory in preparation for a “network homes” log in.
LikeLike